In order to answer the question of how to protect GNSS signals from being jammed or spoofed, it is perhaps prudent to first define what GNSS, jamming and spoofing are.
GNSS Signals
GNSS stands for Global Navigation Satellite System which uses a network of satellites covering the whole planet in order to provide positioning and timing information to GNSS receivers on earth. There are 4 GNSS’s in operation: GPS (American), GLONASS (Russian), GALILEO (European) and BEIDOU (Chinese). These 4 systems are completely independent of one another, with separate infrastructure in place; however, their principles of operation are the same [1].
Its ability for global coverage of positioning information is a result of encapsulating the earth with a sufficient number of satellites. Additionally, maintaining a highly accurate and stable timing synchronization system enables a process called trilateration to define its position with relation to the satellites.
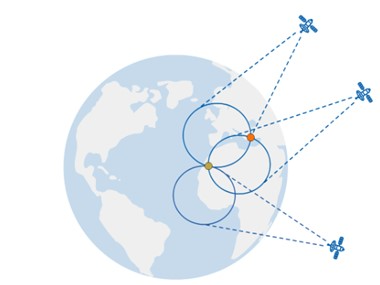
The speed of the satellite signal is known to be the speed of light and through clock cycles, the time it takes for the signal to reach the receiver is also known, therefore the distance to a satellite can be calculated. Due to the known distance between a receiver and a satellite, the coverage of a satellite appears in the form of a circle. When a second and third satellite can be seen by the GNSS receiver, it is possible to pinpoint a location as the intersection of all three satellite signal coverages due to the known distance from each of the satellites. This is known as trilateration. Three satellites are adequate for a 3D position estimate. A fourth satellite is needed for the timing connection [2].
One of the main problems with GNSS signals, is that by the time the signal reaches the GNSS receiver, it is incredibly weak, becoming incredibly vulnerable to jamming or spoofing attempts.
GNSS Jamming vs GNSS Spoofing
The main difference between GNSS jamming and GNSS spoofing is the composition of the signal and the effect it has on the receiver. Jamming is made possible due to the weak GNSS receiver signal; GNSS jamming occurs when a strong signal (usually originating from the ground) masks the weak signal being received from the satellites. This will happen when there is significant interference occurring in the frequency bands of the GNSS signal, which can be either deliberate or not.
Whereas, spoofing is much more deliberate and potentially more damaging because it involves a conscious effort to mimic the GNSS signal by creating a GNSS coded/structured signal on earth aimed to misdirect the GNSS receiver. This will fool the GNSS receiver into thinking it is in a location different from reality. One of the reasons this is potentially more damaging than a jamming attack is that the receiver may not be aware of the false coordinates it is being given. On the other hand, with a jamming attack, it is obvious when the receiver loses signal [3].
Not only is it possible to completely obscure a GNSS signal, but if the jamming/spoofing is only partially successful, signal degradation can still occur, causing an increase in the error for positioning information.
Anti Jamming Technology
It is possible to take measures to improve the resilience of a system to jamming or spoofing attempts. TUALCOM is a world leading expert in this field after developing anti jamming products using adaptive beamforming technology.
The general principle of this technology is to receive a GNSS signal from the satellites and suppress the signal originating from the jamming/spoofing source. Whether jamming or spoofing is being attempted makes no difference to the principle of operation, meaning that TUALCOM’s anti-jamming product line is resilient to both spoofing and jamming alike.
One antenna is configured to receive the GNSS signal from the satellite. The digital antenna control unit (DACU) will focus on receiving the GNSS signal. TUALCOM has products with the capability to use up to 15 other antennas for suppressing up to 15 different direction jamming sources. The DACU will determine which direction the interference is originating from and create a null in the same direction to suppress any unwanted interference.
The form factor of TUALCOM’s anti-jamming product line is what ensures its position at the top of the market. Its jamming suppression capabilities with respect to its size is second to none, allowing for drones to take advantage of this technology when previously the form factor of this technology would not allow this. When comparing TUALCOM’s products to the rest of the market, the most noticeable improvements are the size, weight and power (SWAP) characteristics, providing the ability to implement this technology on a wide range of platforms.



